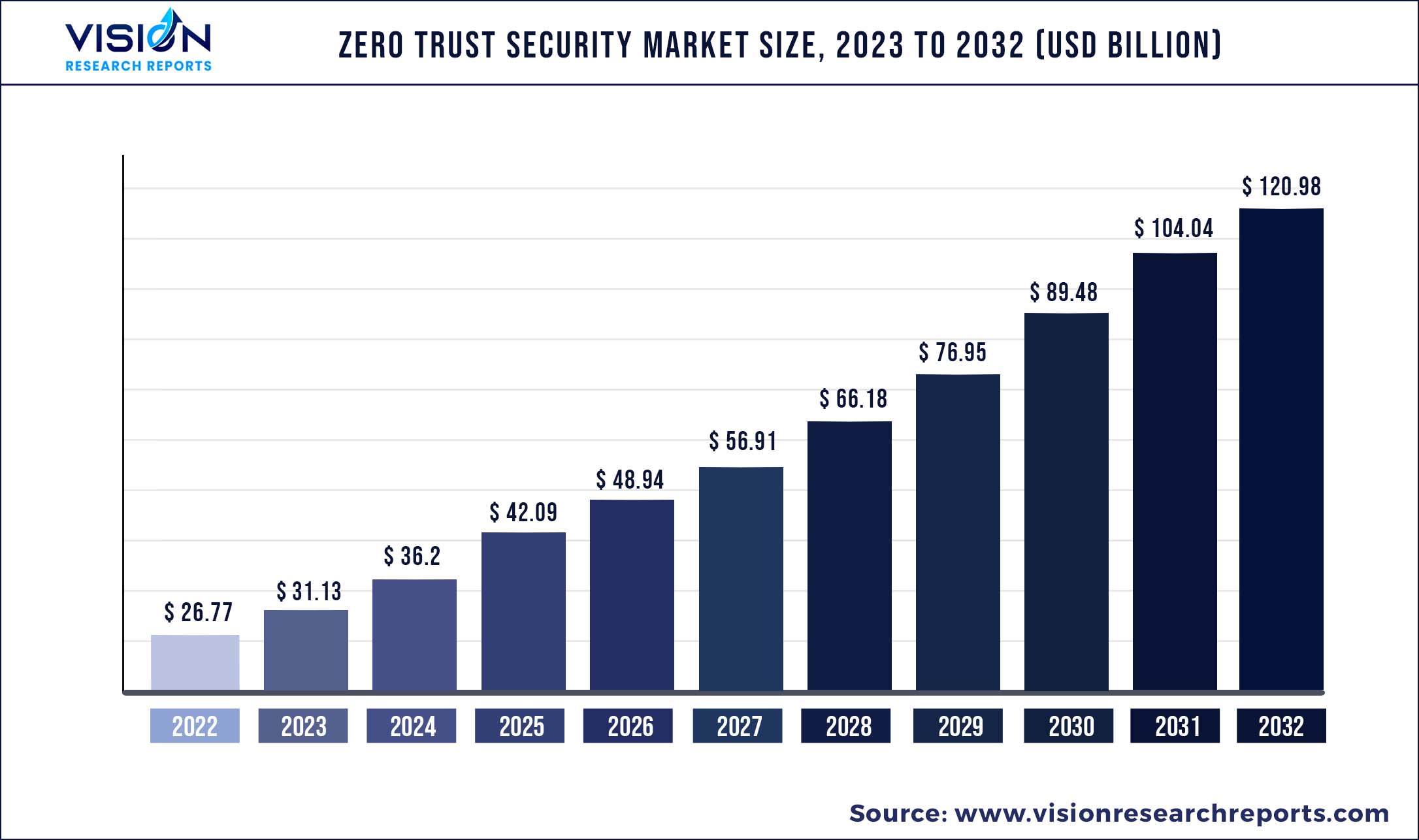
The global zero trust security market size was estimated at around USD 26.77 billion in 2022 and it is projected to hit around USD 120.98 billion by 2032, growing at a CAGR of 16.28% from 2023 to 2032.
Key Pointers
Report Scope of the Zero Trust Security Market
| Report Coverage | Details |
| Market Size in 2022 | USD 26.77 billion |
| Revenue Forecast by 2032 | USD 120.98 billion |
| Growth rate from 2023 to 2032 | CAGR of 16.28% |
| Base Year | 2022 |
| Forecast Period | 2023 to 2032 |
| Regions Covered | North America, Europe, Asia Pacific, Latin America, Middle East & Africa |
| Companies Covered | Cisco Systems, Inc.; Akamai Technologies; Palo Alto Networks; Check Point Software Technologies; Trend Micro, Inc.; IBM Corp.; Symantec Corp.; FireEye, Inc.; McAfee Corp.; Forcepoint; Microsoft Corp.; VMWare, Inc.; Fortinet; Cloudflare, Inc.; SonicWall |
The proliferation of endpoint devices, coupled with the rising adoption of cloud technology, has triggered the need for implementing a zero-trust security framework. Lately, businesses are thriving on networking technology and computerized systems, which are prone to attack and vulnerable to unauthorized access. Moreover, the remote working policies, due to the COVID-19 pandemic, have further raised the need for a secured architecture framework that would enforce multi-factor authentication for accessing crucial data. Thereby, the need to secure complex networks, increase network administration visibility, and combat the internal and external threat from unauthorized access is driving the demand for security solutions and is expected to boost the market growth over the forecast period.
The continued evolution in technologies and internet connectivity over the years has increased the potential impact of internal and external threats. The assessment of reported attacks and intrusions suggests an increase in records-exposed rate and data breaches over the years. Furthermore, attacks, such as WannaCry ransomware, have become complex and disruptive, enabling unauthorized access and resulting in data and revenue loss. With an average cost of USD 4 million incurred from a data breach in a company, vulnerability assessment tools have become essential to scan and identify internal and external vulnerabilities. With the changing landscape of cyber attacks and the related consequences, investments in emerging technologies, such as analytics and Artificial Intelligence (AI), are growing in the vulnerability assessment industry. Furthermore, with continued efforts toward spending on innovative vulnerability management solutions, a downward trend in malicious attacks has been observed. This suggests that the end-users are more prepared for tackling vulnerability attacks, and with the increased investments as an effort toward security strategy, the zero-trust security market is expected to register significant growth over the forecast period.
The lack of in-house skilled professionals is propelling organizations to outsource security services. Security services for implementing a zero-trust security model allow professionals to assist in delivering security protection as a Security-as-a-Service (SaaS) model without any requirements for additional staffing and hardware. Organizations are struggling to keep their network secured owing to the rapidly evolving Wide Area Network (WAN) environment and the growing complexity of enterprise networks. The need for more vigilant attempts to secure enterprise networks and ensure multi-layered security is driving the adoption of solutions offered to implement a zero-trust security model.
The COVID-19 pandemic has helped enterprises realize the importance of a zero-trust environment to secure their crucial data. The IT security environment has changed drastically with employees working remotely using vulnerable networking infrastructure. This has posed difficulty across enterprises to maintain a network perimeter-centric view of security, thereby allowing tech-savvy hackers to target unsecured systems with phishing attacks. The implementation of a zero-trust security approach ensures that only authorized persons have a distinct level of access, which is assessed continuously without adding friction for the user. As the pandemic has drained enterprises of their target revenues for the year 2021 - 2022, the investment has been comparatively lower than expected by solution providers. However, post the pandemic, companies are looking forward to continuing working remotely and would be investing heavily in implementing the zero trust architecture.
Zero Trust Security Market Segmentations:
| By Security Type | By Deployment | By Organization Size |
By Authentication |
By Application Area |
|
Network Security Data Security Endpoint Security Cloud Security Others |
On-premises Cloud |
SMEs Large Enterprise |
Single-factor Authentication Multi-factor Authentication |
IT & Telecom BFSI Healthcare Retail Others |
Chapter 1. Introduction
1.1. Research Objective
1.2. Scope of the Study
1.3. Definition
Chapter 2. Research Methodology
2.1. Research Approach
2.2. Data Sources
2.3. Assumptions & Limitations
Chapter 3. Executive Summary
3.1. Market Snapshot
Chapter 4. Market Variables and Scope
4.1. Introduction
4.2. Market Classification and Scope
4.3. Industry Value Chain Analysis
4.3.1. Raw Material Procurement Analysis
4.3.2. Sales and Distribution Channel Analysis
4.3.3. Downstream Buyer Analysis
Chapter 5. COVID 19 Impact on Zero Trust Security Market
5.1. COVID-19 Landscape: Zero Trust Security Industry Impact
5.2. COVID 19 - Impact Assessment for the Industry
5.3. COVID 19 Impact: Global Major Government Policy
5.4. Market Trends and Opportunities in the COVID-19 Landscape
Chapter 6. Market Dynamics Analysis and Trends
6.1. Market Dynamics
6.1.1. Market Drivers
6.1.2. Market Restraints
6.1.3. Market Opportunities
6.2. Porter’s Five Forces Analysis
6.2.1. Bargaining power of suppliers
6.2.2. Bargaining power of buyers
6.2.3. Threat of substitute
6.2.4. Threat of new entrants
6.2.5. Degree of competition
Chapter 7. Competitive Landscape
7.1.1. Company Market Share/Positioning Analysis
7.1.2. Key Strategies Adopted by Players
7.1.3. Vendor Landscape
7.1.3.1. List of Suppliers
7.1.3.2. List of Buyers
Chapter 8. Global Zero Trust Security Market, By Security Type
8.1. Zero Trust Security Market, by Security Type, 2023-2032
8.1.1. Network Security
8.1.1.1. Market Revenue and Forecast (2020-2032)
8.1.2. Data Security
8.1.2.1. Market Revenue and Forecast (2020-2032)
8.1.3. Endpoint Security
8.1.3.1. Market Revenue and Forecast (2020-2032)
8.1.4. Cloud Security
8.1.4.1. Market Revenue and Forecast (2020-2032)
8.1.5. Others
8.1.5.1. Market Revenue and Forecast (2020-2032)
Chapter 9. Global Zero Trust Security Market, By Deployment
9.1. Zero Trust Security Market, by Deployment, 2023-2032
9.1.1. On-premises
9.1.1.1. Market Revenue and Forecast (2020-2032)
9.1.2. Cloud
9.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 10. Global Zero Trust Security Market, By Organization Size
10.1. Zero Trust Security Market, by Organization Size, 2023-2032
10.1.1. SMEs
10.1.1.1. Market Revenue and Forecast (2020-2032)
10.1.2. Large Enterprise
10.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 11. Global Zero Trust Security Market, By Authentication
11.1. Zero Trust Security Market, by Authentication, 2023-2032
11.1.1. Single-factor Authentication
11.1.1.1. Market Revenue and Forecast (2020-2032)
11.1.2. Multi-factor Authentication
11.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 12. Global Zero Trust Security Market, By Application Area
12.1. Zero Trust Security Market, by Application Area, 2023-2032
12.1.1. IT & Telecom
12.1.1.1. Market Revenue and Forecast (2020-2032)
12.1.2. BFSI
12.1.2.1. Market Revenue and Forecast (2020-2032)
12.1.3. Healthcare
12.1.3.1. Market Revenue and Forecast (2020-2032)
12.1.4. Retail
12.1.4.1. Market Revenue and Forecast (2020-2032)
12.1.5. Others
12.1.5.1. Market Revenue and Forecast (2020-2032)
Chapter 13. Global Zero Trust Security Market, Regional Estimates and Trend Forecast
13.1. North America
13.1.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.1.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.1.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.1.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.1.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.1.6. U.S.
13.1.6.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.1.6.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.1.6.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.1.6.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.1.7. Market Revenue and Forecast, by Application Area (2020-2032)
13.1.8. Rest of North America
13.1.8.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.1.8.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.1.8.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.1.8.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.1.8.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.2. Europe
13.2.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.2.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.2.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.2.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.2.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.2.6. UK
13.2.6.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.2.6.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.2.6.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.2.7. Market Revenue and Forecast, by Authentication (2020-2032)
13.2.8. Market Revenue and Forecast, by Application Area (2020-2032)
13.2.9. Germany
13.2.9.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.2.9.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.2.9.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.2.10. Market Revenue and Forecast, by Authentication (2020-2032)
13.2.11. Market Revenue and Forecast, by Application Area (2020-2032)
13.2.12. France
13.2.12.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.2.12.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.2.12.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.2.12.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.2.13. Market Revenue and Forecast, by Application Area (2020-2032)
13.2.14. Rest of Europe
13.2.14.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.2.14.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.2.14.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.2.14.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.2.15. Market Revenue and Forecast, by Application Area (2020-2032)
13.3. APAC
13.3.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.3.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.3.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.3.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.3.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.3.6. India
13.3.6.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.3.6.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.3.6.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.3.6.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.3.7. Market Revenue and Forecast, by Application Area (2020-2032)
13.3.8. China
13.3.8.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.3.8.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.3.8.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.3.8.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.3.9. Market Revenue and Forecast, by Application Area (2020-2032)
13.3.10. Japan
13.3.10.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.3.10.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.3.10.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.3.10.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.3.10.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.3.11. Rest of APAC
13.3.11.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.3.11.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.3.11.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.3.11.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.3.11.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.4. MEA
13.4.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.4.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.4.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.4.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.4.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.4.6. GCC
13.4.6.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.4.6.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.4.6.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.4.6.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.4.7. Market Revenue and Forecast, by Application Area (2020-2032)
13.4.8. North Africa
13.4.8.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.4.8.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.4.8.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.4.8.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.4.9. Market Revenue and Forecast, by Application Area (2020-2032)
13.4.10. South Africa
13.4.10.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.4.10.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.4.10.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.4.10.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.4.10.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.4.11. Rest of MEA
13.4.11.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.4.11.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.4.11.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.4.11.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.4.11.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.5. Latin America
13.5.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.5.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.5.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.5.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.5.5. Market Revenue and Forecast, by Application Area (2020-2032)
13.5.6. Brazil
13.5.6.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.5.6.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.5.6.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.5.6.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.5.7. Market Revenue and Forecast, by Application Area (2020-2032)
13.5.8. Rest of LATAM
13.5.8.1. Market Revenue and Forecast, by Security Type (2020-2032)
13.5.8.2. Market Revenue and Forecast, by Deployment (2020-2032)
13.5.8.3. Market Revenue and Forecast, by Organization Size (2020-2032)
13.5.8.4. Market Revenue and Forecast, by Authentication (2020-2032)
13.5.8.5. Market Revenue and Forecast, by Application Area (2020-2032)
Chapter 14. Company Profiles
14.1. Cisco Systems, Inc.
14.1.1. Company Overview
14.1.2. Product Offerings
14.1.3. Financial Performance
14.1.4. Recent Initiatives
14.2. Akamai Technologies
14.2.1. Company Overview
14.2.2. Product Offerings
14.2.3. Financial Performance
14.2.4. Recent Initiatives
14.3. Palo Alto Networks
14.3.1. Company Overview
14.3.2. Product Offerings
14.3.3. Financial Performance
14.3.4. Recent Initiatives
14.4. Check Point Software Technologies
14.4.1. Company Overview
14.4.2. Product Offerings
14.4.3. Financial Performance
14.4.4. Recent Initiatives
14.5. Trend Micro, Inc.
14.5.1. Company Overview
14.5.2. Product Offerings
14.5.3. Financial Performance
14.5.4. Recent Initiatives
14.6. IBM Corp.
14.6.1. Company Overview
14.6.2. Product Offerings
14.6.3. Financial Performance
14.6.4. Recent Initiatives
14.7. Symantec Corp.
14.7.1. Company Overview
14.7.2. Product Offerings
14.7.3. Financial Performance
14.7.4. Recent Initiatives
14.8. FireEye, Inc.
14.8.1. Company Overview
14.8.2. Product Offerings
14.8.3. Financial Performance
14.8.4. Recent Initiatives
14.9. McAfee Corp.
14.9.1. Company Overview
14.9.2. Product Offerings
14.9.3. Financial Performance
14.9.4. Recent Initiatives
14.10. Forcepoint
14.10.1. Company Overview
14.10.2. Product Offerings
14.10.3. Financial Performance
14.10.4. Recent Initiatives
Chapter 15. Research Methodology
15.1. Primary Research
15.2. Secondary Research
15.3. Assumptions
Chapter 16. Appendix
16.1. About Us
16.2. Glossary of Terms
 Cross-segment Market Size and Analysis for
Mentioned Segments
Cross-segment Market Size and Analysis for
Mentioned Segments
 Additional Company Profiles (Upto 5 With No Cost)
Additional Company Profiles (Upto 5 With No Cost)
 Additional Countries (Apart From Mentioned Countries)
Additional Countries (Apart From Mentioned Countries)
 Country/Region-specific Report
Country/Region-specific Report
 Go To Market Strategy
Go To Market Strategy
 Region Specific Market Dynamics
Region Specific Market Dynamics Region Level Market Share
Region Level Market Share Import Export Analysis
Import Export Analysis Production Analysis
Production Analysis Others
Others